In case you haven’t noticed, we’re in the middle of a seismic shift in end-user computing. Gone are the days of desktop computers, chained to a piece of furniture and attached over a local network to a file server and a print spooler. The new watchwords are mobility and flexibility, as more and more workers are getting accustomed to tablet computers, smartphones, laptops, and the ability to access their data from anywhere with an Internet connection. More and more often, employees want to have this sort of experience at work as well as at home, even going so far as to use their personally-owned equipment on their employer’s network.
From the employee’s point of view, it just makes sense. Given the choice between a boring two-year-old HP or Dell desktop computer running the locked-down corporate image of Vista and a sleek new MacBook, most people are going to choose the latter. Especially if they’re already Macintosh enthusiasts.
From the employer’s point of view, it also makes sense – if your employees are happy, they’re going to more productive. And if having exactly the computing environment they want, on their own dime, makes them happy; well, who would stand in the way? The company is saving money from the technology budget, the employees can choose the tools they’re most comfortable with. It’s a win-win situation.
However, things can go south in a hurry. Little or no input over employee equipment means that it’s difficult to maintain a solid security posture. Clients need to be treated as hostile and anonymous until proven otherwise, a clear break from the tradition of trusted clients that have been vetted by IT. If you decide to move in this direction in your own company, here are a few principles and suggestions that you should keep in mind.
- Have Appropriate Policies, And Publicize Them
Many of the things that I am going to suggest depend on writing clear, concise policies and educating your end users about them. When users are in charge of their own workstations, they need to understand the consequences of their actions. Central IT is not able to provide the safety net that they have in the past when they don’t have any control over the clients on the network.
Policies need to be inclusive, rather than exclusive – that is, they should include requirements rather than restrictions. Also, they should be as technology-agnostic as possible. This makes them easier to keep current, and harder to find loopholes in.
“All mobile devices connecting to the Exchange environment must be ActiveSync compatible.” – Good.
“Mobile devices running Windows Mobile are forbidden on the corporate network.” – Bad. What happens when Microsoft changes the name of their mobile OS? And what if there’s another OS that you’re banning for the same reason?
- Guard Network Access Jealously
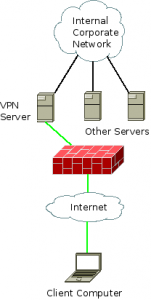
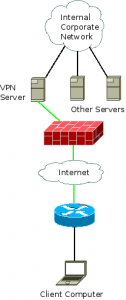
If users are going to be showing up with their own devices and plugging them into your network, you need some way to know who owns what. At the very least, implement a registration system like Netreg so that you can track MAC addresses and who owns them. (I know that this is trivially spoofed, but it’s better than nothing.) A better solution would be to roll out 802.1x on both the wired and wireless networks, forcing authentication against a centralized RADIUS server at connection time. An ideal solution would be a full-blown Network Access Control implementation, whether it’s something commercial like Cisco Clean Access or Bradford Campus Manager, or an open-source solution like Packetfence. A Network Access Control (NAC) system not only registers the devices, but can evaluate their security posture to allow or disallow access to the network.
So, if you have a site license for an antivirus product, and you don’t want people connecting to your network without it, a NAC can make that happen. It may seem like an unnecessary investment, until the first time there’s a malware outbreak on your network and you have no way to isolate infected machines.
Also, it is appropriate to treat every client as potentially infected or hostile. Use IDS/IPS systems to monitor traffic, use host-based firewalling to protect servers from clients that haven’t been whitelisted, use egress filtering and log flow data at your border.
- Have A Proper Backup System
Imagine this scenario – you find out that one of your employees has been giving proprietary data to a competitor. This person works in sales, and has a tremendous amount of vital customer data in his possession. On his personally-owned laptop. Which you would have no legal right to access, at least not without lawyers getting involved.
Uh-oh.
Products like Microsoft Data Protection Manager and Apple Time Machine should be used to take regular, periodic backups of corporate data stored on personally owned computers. If data is the lifeblood of your business, and for most people it is, then there needs to be at least one copy of that data on a machine that’s owned by the business. This is one of those policies that I was talking about earlier.
Your company needs to have a policy governing encryption of sensitive data, regardless of who owns the hardware. Modern operating systems all come with encryption options – Apple’s FileVault, Microsoft’s BitLocker, the LUKS capability built into most Linux distributions. Aside from those, there are a wealth of third-party tools like PGP Desktop or Utimaco that can be installed and used. Anything carrying sensitive data needs to be properly secured, especially if that “anything” is spending sixteen hours a day outside of the office and unaccounted for with its owner. Anything containing “work data” needs to be encrypted; you don’t want to be the business on the front page of the local paper after someone in Accounting leaves his Thinkpad in a taxi.
This goes for mobile phones, as well. A system like Blackberry Server Express or Microsoft Exchange allows security requirements to be pushed down to associated handsets. At the very least, passwords should be required after a short lockout period, and employees should be required to report a lost handset immediately so that it can be remotely wiped.
- Use Remote Desktop Capabilities
For truly sensitive information, it might be wise not to let it leave your corporate servers at all. Technologies like Citrix Access Gateway or Microsoft Remote Desktop can be used to allow access to a desktop shell without ever moving data across the link to the client machine. I would recommend using multi-factor authentication, with ID tokens or smart cards, to mitigate the risk of a compromised machine leaking authentication credentials to your terminal server environment.
First, the bad news: there’s no way to make a network of dissimilar, un-vetted devices completely secure. It is entirely possible for an end user to simply disregard policy and wreak tremendous havoc on your network before you’re able to stop him. If you’re able to stop him.
But here’s the good news: a network that is designed to actively deal with the threat of a rogue client is much more likely to withstand an internal attack that one designed around the traditional trusted-machines-behind-a-single-firewall model. Implementing these technical suggestions, along with dissemination of appropriate policy, could easily make a Bring-Your-Own-Hardware network more reliable and robust than its traditional counterparts, even with employees choosing their own gear.



 Posted by matt
Posted by matt