HP has been remarkably quiet since their acquisition of Palm last year, but that might be changing soon – it looks like they will be releasing a new tablet as well as a pair of new phones. It will be interesting to see if the WebOS platform, which was an impressive product doomed by Palm’s atrocious marketing techniques, can gain a foothold in the iOS dominated smartphone and tablet market.
Openfiler
February 8, 2011If you’re looking to centralize the data storage in your enterprise – perhaps in response to a particularly persuasive and insightful article you read on the Internet somewhere – you might want to take a look at the Openfiler project.
Openfiler is a Linux distribution designed to be used as the interface for a Network Attached Storage device. Essentially, it is used to build a storage pool that the other computers in your environment can connect to in order to share data. It supports NFS, SMB, FTP, iSCSI, and a tremendous number of other acronyms. The only real annoyance is that the otherwise excellent web GUI doesn’t include any tools for setting up an iSCSI initiator, so that must be done from the command line.
HBGary Breach
February 7, 2011According to several sources, including this article at eWeek, security firm HBGary Federal is paying the price for taunting the hacktivist group Anonymous. A few days ago, HBGary claimed to have uncovered information about the leadership structure and identities of Anonymous. In retaliation, the group compromised the HBGary network, posted internal emails, and generally caused havoc.
(Update: Apparently, the root of the compromise was a social engineering attack. Someone was convinced that they were sending authentication credentials to a host behind the firewall to a legitimate user; apparently, they were incorrect. The idea that a “security” firm would be sending unencrypted email with account details in response to an unvalidated, unsigned message boggles my mind.)
Hoover Dam
February 7, 2011Part of the hype for the current “Internet Kill Switch” legislation has been evocative images of the Hoover Dam. Clearly, nobody wants the floodgates of the Hoover Dam to open due to an Internet security breach – it’s a great image, because it’s like something out of a Bond movie. So the backers of the bill have been painting that picture and hoping that the visceral dread it evokes will help carry the bill through Congress.
Only one problem – the Hoover Dam, according to the people who actually manage it, isn’t connected to the Internet.
Next thing you know, villains won’t have eyepatches and cats. What a world.
Definition Monday: Intrusion Detection Systems
February 7, 2011Welcome to Definition Monday, where we define and explain a common technology or security concept for the benefit of our less experienced readers. This week: Intrusion Detection Systems.
An Intrusion Detection System, often referred to with the abbreviated “IDS”, is exactly what it sounds like. It is a piece of hardware or software that listens to data changes or traffic in a particular environment, watching for suspicious or exploitative trends. Think of it like the high-tech version of a motion detector light on a house; it passively monitors the environment until something triggers it, and then performs a specified task. Just like the motion detector will turn on the light, the IDS will log the problem, generate an SMS text message to an administrator, or email an affected user.
Broadly speaking, there are two common classes of IDS – Network-based IDS systems (NIDS) and Host-based IDS systems (HIDS).
Network-based IDS (NIDS)
A NIDS system passively monitors the traffic in an environment, watching for certain patterns that match a defined set of signatures or policies. When something matches a signature, an alert is generated – the action that occurs then is configurable by the administrator.
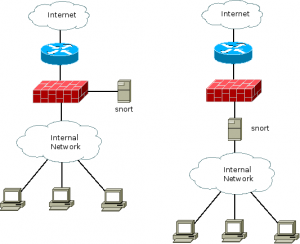
The most common NIDS in use these days is probably Snort, an open-source solution written by Marty Roesch and maintained by his company, Sourcefire. Snort is capable of acting as either a passive eavesdropper or as an active in-line part of the network topology. In this diagram, the lefthand example is a passive deployment, the right is in-line.
As you can see in the example on the left, the computer running snort is connected to the firewall – the firewall would be configured with a “mirror” or “spanning” port that would essentially copy all of the incoming and outgoing traffic to a particular interface for the snort software to monitor. This way, any suspicious traffic passing the border of the network would be subject to examination.
In the example on the right, the traffic is passing directly through the snort machine, using two Ethernet interfaces. This is an excellent solution for environments where a mirror port is unavailable, such as a branch office using low-end networking equipment that can’t provide the additional interface.
(It is important to note that a NIDS should be carefully placed within the network topology for maximum effectiveness. If two of the client machines in these diagrams are passing suspicious traffic between them, the snort machine will not notice; it only sees traffic destined for the Internet. It is always possible, of course, to run multiple NIDS systems and tie all of the alerts into one console for processing so as to eliminate these blind spots.)
Because of its large install base, rules for detecting new threats are constantly being produced and published for free usage on sites like Emerging Threats. If you want to be alerted when a host on your network is connecting a known botnet controller, for example, the up-to-the-minute rules for this can be downloaded from ET. The same goes for signatures of new worms and viruses, command-and-control traffic, and more.
So a NIDS is an excellent tool for detecting when a host on your network has been compromised or is otherwise producing suspicious traffic. But what about exploits that don’t cause traffic generation? If someone compromises your e-commerce server, for example, and installs a rootkit and starts modifying the code used to generate web pages, your NIDS will be none the wiser. For more careful monitoring of individual high-priority hosts, you would use a HIDS.
Host-based IDS (HIDS)
While a NIDS watches the traffic on a network segment, HIDS watches the activities of a particular host. A common open-source HIDS system is OSSEC, named as a contraction of Open Source Security.
OSSEC will monitor the Windows Registry, the filesystem of the computer, generated logs, and more, looking for suspicious behavior. As with a NIDS, an alert will be generated by any suspicious activity on the host and the results of the alert can be set by the administrator. If a process is attempting to modify the documents on your main web server, for example, OSSEC can kill that process, lock out the account that launched it, and send an email to the system administrator’s cell phone. It’s a remarkably flexible and impressive system.
Much like a NIDS, the placement of HIDS software needs to be carefully planned. You don’t want to receive an alert every time a file is accessed on a file server, for example; your administrator will be overwhelmed, and will simply stop reading alerts altogether. The system has to be carefully configured and the monitored behaviors pruned to as to eliminate false alarms and ensure that true security issues are noticed and alerted properly.
Password Dictionaries
February 6, 2011Password cracking tools like John the Ripper work by generating potential passwords and then matching them against the system being tested. These potential passwords come from a “dictionary” – a list of words that are assumed to be potential passwords, that are used as seeds to generate permutations that a user might have selected.
But what’s better than permutations a user might have selected? How about password lists from breaches, so that we can see what users ACTUALLY use.
According to the site, these passwords will crack roughly 5% of user accounts on a given system. If you’re using one of them, change it now.
123456 12345 123456789 password iloveyou princess 1234567 12345678 abc123 nicole daniel babygirl monkey
Adobe Reader Patches
February 5, 2011It looks like this will be a busy patch week – in addition to the usual Patch Tuesday fun from Microsoft, Adobe has announced a set of patches for their Reader product on all supported operating systems. As malicious PDF files are one of the most common exploit launching techniques these days, it would be prudent to begin planning your patching operations.
Hack Chrome, Win $20k
February 4, 2011The annual Pwn2Own contest is next month in Vancouver, and there’s an additional prize this year. As always, the latest copies of Firefox, Safari, and IE will be available as targets – hackers who manage to exploit the browser in a significant way will win a cash prize and the laptop that the browser was running on at the time. For the first time, though, Google’s Chrome is available as a target, and they’ve staked an additional $20,000 as prize money for anyone able to break their product.
Let the games begin. It seems like every year, someone manages to trot out a zero-day exploit and win the contest on at least one platform; it will be interesting to see how Chrome fares against dedicated competition like this.
Tandberg Default Root Account
February 3, 2011Cisco has announced that Tandberg E, EX, and C series Personal Video Endpoints running pre-TC4.0.0 software shipped with a default root account with no password.
Well, that’s not great.
Workaround and mitigation details at the link.
Dealing With The Snowpocalypse
February 3, 2011Like most of the continental United States, Buffalo was expected to suffer the brunt of a tremendous storm this week. Fortunately, we escaped relatively unscathed – despite dozens of schools and businesses preemptively canceling their workdays on Wednesday, the anticipated feet of snow and ice never arrived.
Despite this, though, I imagine that a lot of businesses in the area were taking a long look at their disaster plans. Just because some employees are unable to get to the office doesn’t mean that the business should simply close down for the day. In that vein, I wanted to mention two topics that need to be addressed if you want work to be possible outside of the physical boundaries of your business location.
Centralize Your Data
Too many small businesses work in an ad-hoc fashion, without any centralized file storage. This means that important documents are only available on a particular person’s workstation, or are squirreled away on a flash drive or floppy disk in the back of a locked drawer in the author’s desk. One of the first steps toward making your information infrastructure more robust is to properly centralize and organize your data. This has several advantages:
- A single central data store is much easier to back up than a collection of random workstations.
- A single employee leaving or changing jobs will not affect the information that he or she was handling.
- A single workstation with a hardware failure can be easily replaced, since user data won’t need to be replicated from the old drive.
- Most importantly, an individual employee’s work is no longer dependent on a single physical workstation.
Think about it – what is the biggest single factor that keeps knowledge employees from working at home now? It’s that they don’t have access to their data – memos, notes, project lists, legacy files, and the like. Most people have a computer and some sort of Internet access at home, but without data access, that doesn’t mean that they can work effectively. And without centralization of data, they can’t get that data access.
Now, centralization of data can mean many different things depending on what sort of data they need to handle. If it’s primarily textual or documentary data, a wiki like MediaWiki or Confluence might be a good option. For data that many people are editing and collaborating on, a version control system like Subversion might be appropriate. For general file storage, a file server built on Ubuntu and Samba might be your best bet. Beyond choosing the appropriate methodology for the data, the important thing is realizing the necessity of having all of the data in one place.
Deploy a VPN
Once all of the data is properly centralized, that means that any computer with proper access to your local network will be able to access it. Under normal business circumstances, this means that your employees can access or share their work from anywhere in the building. This is good – it makes work more efficient and flexible. More importantly, combining this centralized data with a Virtual Private Network means that your employees can access their data from anywhere on the Internet. This is even better.
Let’s look at the example of Alice and Bob. Alice and Bob are collaborating on a piece of documentation – Alice has deployed a new piece of equipment, and Bob is in charge of writing up the procedure for using it.Each time Bob writes a new section of the guide, Alice has to approve it.
Under the old model, where everything is stored on local hard drives, the writing of this documentation grinds to a halt whenever Alice or Bob is out of the office. After all, if Bob has changed something, and then leaves work early, the data is stored on his computer and Alice can’t confirm that it’s been changed or that the changes are accurate. A lot of time is wasted waiting for an opportunity for the two of them to work together.
In the new model, where data is centralized, Alice doesn’t have to wait for Bob – the new data is stored on some central server, like a wiki, and so she can continue checking its accuracy without his needing to be present. But if any changes need to be made, again, the project grinds to a halt. Bob needs to be on-site for the process to continue.
But if we combine this centralized data with a VPN, then Bob can work from anywhere on the Internet. A snow day, like the one that was anticipated this week, shouldn’t slow anything down; Bob can log into the business VPN, gain access to the central data store, and continue working on the documentation. Alice can do the same. And rather than losing a day of productivity to a snowstorm or a driving ban, they can finish the documentation and be ready to move on to another task when the office is open again.
Data centralization and VPN deployment are two of the many services that we offer. If you would like help disaster-proofing your business’s data, please click on the Contact button to the left and send us an email.



 Posted by matt
Posted by matt